
IT Network Security: Mainframe Security Best Practices for Meeting Compliance Regulations and Minimizing Data Vulnerabilities

Considering that mainframes handle 68 percent of the world’s production IT workloads, mainframe security is a huge component of your overall IT network security.
Mainframers recognize the importance of keeping the mainframe secure. Of the mainframe professionals surveyed in our 2018 mainframe survey, 63 percent said that meeting security and compliance requirements is a top priority.
Reducing security exposures, fulfilling audit requirements, and addressing compliance mandates remains a key initiative for IT executives and IT organizations. The cost of an audit, or even worse failing a compliance mandate, far exceeds the cost of the technologies that can be put into place to help address security and compliance initiatives.
So let’s review common mainframe security challenges and best practices for reducing risk and meeting compliance regulations.
Mainframe security challenges and vulnerabilities
Common mainframe security challenges include data protection, data visibility, and regulatory compliance.
Mainframe encryption
Putting encryption into software solutions that monitor, store and transport data is a big step towards protecting the data on the mainframe. CIO’s and other leaders need to examine all the ways that data is transported, stored, viewed, and used to ensure that the data is thoroughly protected throughout its lifecycle.
Data visibility
In IT network security, the term visibility means an understanding of what is happening in your systems and infrastructure. Visibility through monitoring the mainframe’s machine data provides the foundation for making informed decisions about security.
Regulatory compliance
Compliance regulations provide guidelines for how businesses should be protecting critical customer data. Due to the sensitive nature of this data – and the potential harm to customers if it is not protected – the penalties for organizations that fail to comply with security regulations are quite considerable. The large fines given to businesses that do not meet compliance can cause irrevocable damage to the business both financially and in terms of the organization’s reputation.
Depending on the nature of your business and the customer data stored on your mainframe, you may face numerous mainframe regulation requirements, such as:
- General Data Protection Regulation (GDPR) – GDPR went into effect in May 2018, to protect the personal data of Europeans including how their data is used, stored and accessed.
- Service Organization Control 2 (SOC2) – Developed by the American Institute of CPAs (AICPA), SOC2 requires that companies set and comply with strict information security policies and procedures, encompassing the security, availability, processing, integrity and confidentiality of customer data. Check out our case study: Compliance Rules Lead Client-focused Healthcare Company to Ironstream + Splunk
- Internal Revenue Service Publication 1075 (IRS 1075) – U.S. government agencies and their agents that access federal tax information (FTI) are required to meet IRS Publication 1075 regulations.
Read our white paper
Using Mainframe Log Data for Operational Efficiency & Enhanced Security Across the Enterprise
Understand the key sources of operational and security data in z/OS and how that data can be sent via Ironstream to the Splunk data-integration platform for enhanced enterprise security
Leveraging machine data for improved IT network security
The huge volume of data processed by your mainframes can also help you to detect and stop attacks in real time. For example, it can enable banks to identify a fraudulent credit card transaction and stop while its happening.
Monitoring SMF and z/OS log data
One of top five mainframe trends from our 2018 mainframe survey noted the increased role of machine data (SMF and z/OS log data) in addressing security and compliance mandates. Organizations are looking at leveraging analytics platforms for security and compliance, and they understand the value that SMF and other z/OS log data can provide when coupled with emerging big data analytics platforms including Splunk, Elastic, and Hadoop.
For more about what SMF data and how it can help in mainframe security, read The Ultimate Guide to Mainframe Machine Data
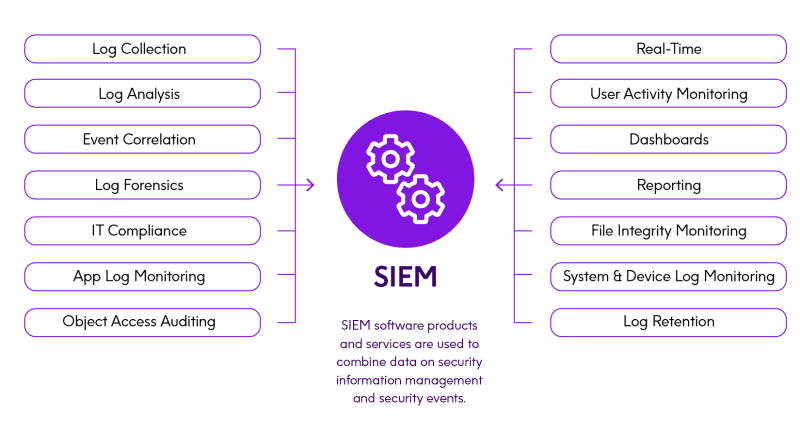
Security Information and Event Management (SIEM)
It was just a few years ago that Security Information and Event Management (SIEM) gaining more attention.
SIEM software products and services combine security information management and security events generated by network hardware and applications to provide real-time analysis of security alerts and threats happening within an organization’s IT infrastructure. The SMF and log files you’re familiar with are an important part of that puzzle, but not all of it.
Precisely Ironstream is the industry’s leading solution for collecting, transforming, and forwarding mainframe log data to external analytics platforms in real time. Ironstream can help you connect mainframe log data to the following analytics platforms:
Real-time monitoring for enhanced security
Capturing user behavior, especially in real-time, is seemingly impossible if you rely only on data you collect from the various logs and SMF data. That’s why Compuware, in conjunction with Precisely and Splunk, recently announced Application Audit, a software tool that aims to transform mainframe cybersecurity and compliance through real-time capture and analysis of user behavior.
“Real-time data collection and analysis is critical in helping IT identify trends and solve issues before they negatively impact the business,” said Chris O’Malley, CEO, Compuware. With Ironstream delivering Compuware Application Audit data to the Splunk platform, organizations can effectively tackle cross-platform cybersecurity and increasingly burdensome global compliance mandates.”


